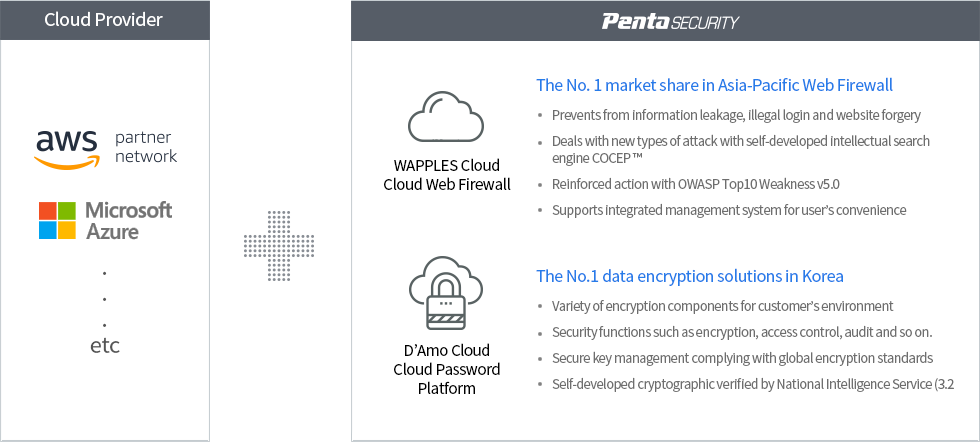
Bespin Global and Penta Security provides you with a safer Cloud Environment.
The three elements of Information Security, Encryption, Web Security and Authentication Security are important in the Cloud.
Many companies are still concerned about the security issues regarding their Cloud adoption.
With Bespin Global and Penta Security, your worries about Cloud security are no longer a concern.
In addition to the complimentary security system of a Cloud provider, Bespin Global improves
customers’ Cloud security level with Web, Data and Authentication Security Technology
provided by Penta Security. In addition, Bespin Global provides a stable business environment to operate on.
Cloud Security Migration Services
Previously, customers had to build an on-premises type security solutions on their own.
In a Cloud environment, it can be built easily and quickly by through managed services.
If you are interested in a secure Cloud environment of Bespin Global and Penta Security, please inquire today.
Manage your cloud environment 24/7/365, with Bespin Global and AhnLab.
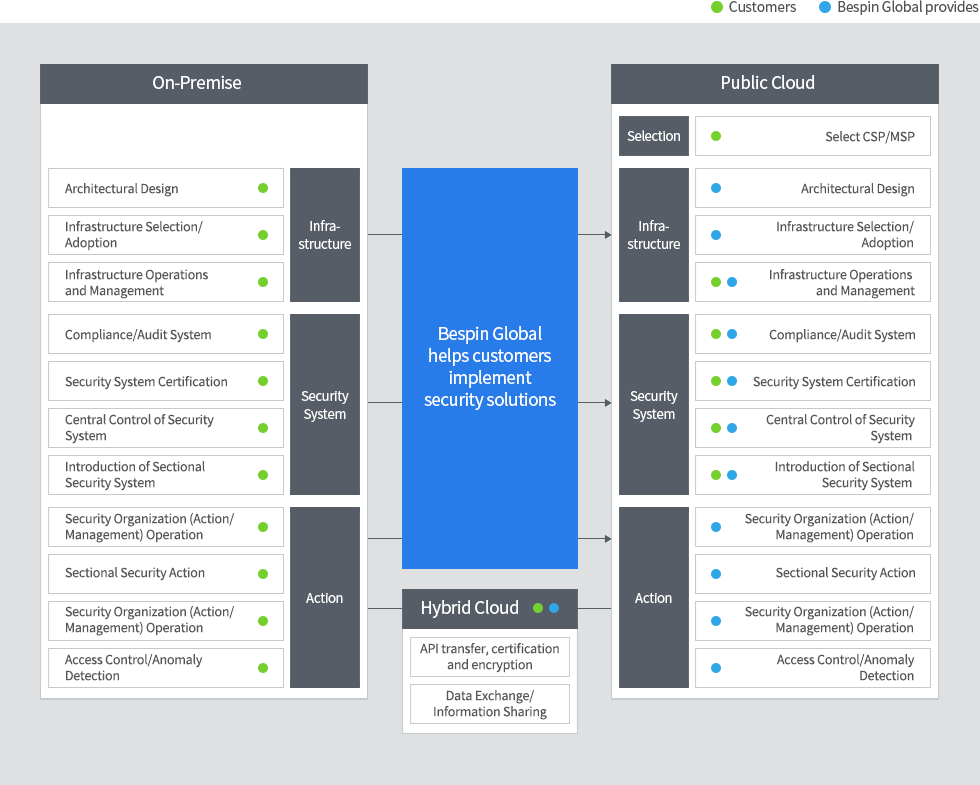
Cloud security is a shared responsibility of cloud users and public cloud providers.
Bespin Global and AhnLab are responsible for ensuring the security of areas that are not covered by public cloud providers.





Cloud Service Provider
Basic services such as computing, storage and database
Network, CDN infrastructure
Components and Scope of Security Control Service
| Controlled Subjects | Cloud | ||||
| I(D)PS Network-wide detection (L3 to L7 layers) | WAF Optimized for web attacks (L7 layers) | Web Shell Service specialized for Web Shell detection | |||
| Analysis |
| ||||
| Scope of Work | Detection of Intrusion Attempts | Response to Infringement Incident | Information Activities | Signature Optimization | Intrusion Prevention |
|
|
|
|
| |
Bespin Global and Trend Micro, a leading provider of server security, have joined to better protect the integrated cloud environment.
Optimized protection for public or hybrid cloud environments not only improves security, but also reduces complexity in management and operation of Bespin Global’s 24/7/365 managed services. Closely integrated modules make it easy to extend the platform to ensure the security of servers, applications, and data across the cloud and hybrid environments.




Cloud and Hybrid Integrated Infrastructure
Cloud and Hybrid Integrated Infrastructure
Deep Security Features
The cloud ensures flexibility, scalability,
and manageability of host-based security
| Criteria | Network-based | Host(SW)-based (Deep Security) |
| Configuration Method | Hardware Appliance (Inline / Tap) | Software Agent (Inline / Tap) |
| Inter-VM Web traffic Monitoring/Detection/Blocking | Impossible | Possible |
| VM Vulnerability Scan | Impossible | Provides web, OS vulnerability scanning capabilities for each VM |
| Virtual Patching | Impossible | Provides web, OS vulnerabilities virtual patching capabilities for each VM |
| Integrated Management | Integrated management of multiple equipment types | Provides server and application visibility with equipment and VM integrated security management |
| Custom Tool Settings | Same policy on all servers | Customized settings based on server usage, OS, and app |
| Performance | Analyze traffic at the network layer and apply the detection tools included in all servers to create performance issues | Optimize performance by applying distributed analysis and essential detection tools to each server layer traffic |
| Impact of False Positives | May occur on all servers if a false positive occurs | Even if a false positive occurs it occurs on only the server that has been applied |
| Failure Response | Influences all traffic if a security function failure occurs | Only the affected server will be handled, not affecting other servers |
| Auto Scaling | Impossible or limited quantity | Unlimited scalability |
Detailed Features
| Antivirus | Provides agentless or agent-based options, which integrate with VMware and other virtual environments. |
| Web Verification | Increases security for web threats on servers and virtual desktops. Protects users and applications by blocking access to malicious URLs with the utilization of web verification feature of Trend Micro's cloud security center (SPN). |
| Intrusion Detection (IPS) | Protects against known vulnerabilities until a patch for exploit is applied.
|
| Firewall | Reduces exposure of physical and virtual servers to attacks.
|
| Integrity Check | Detects and reports in real time when a file or system experiences malicious or unexpected changes.
|